Table of Contents
VORTEX Network Speaker: Fast Track to Setup & Key Features
VORTEX now supports seamless integration with VIVOTEK network speakers, currently AU‑003 and AU‑004. To connect these speakers to the VORTEX cloud, a VIVOTEK RX9502 is required as a bridge device, enabling cloud-based audio management.
Bridge Set-up
System Integrators can follow the RX9502 setup guide to update the device's firmware, converting it into a dedicated VORTEX Cloud Bridge. Once added to your VORTEX organization, the RX9502 is able to detect and bring in LAN‑connected VIVOTEK speakers into the VORTEX portal.
Full Feature Unlock
With speakers paired, end users gain access to:
-
Event-triggered broadcasting — play pre‑loaded warning audio when VORTEX VCA detects events or other regular events
-
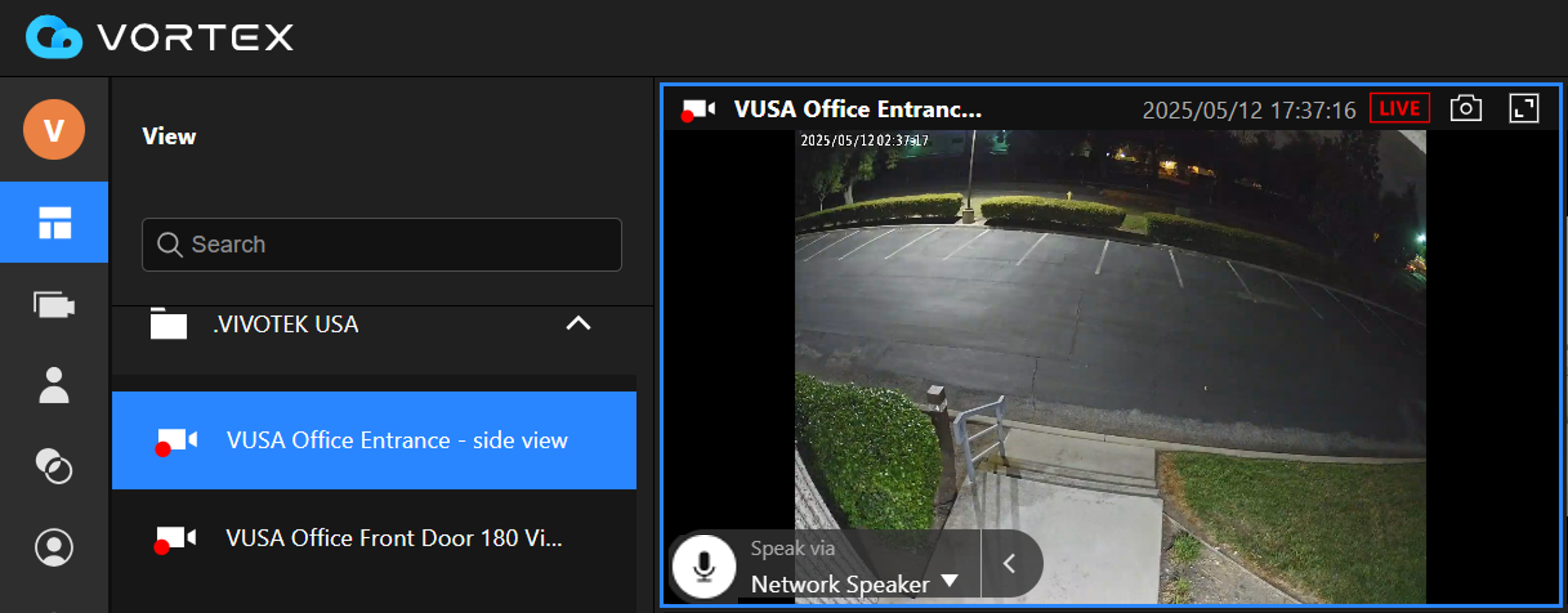
Talk‑down function — live voice communication via VIVOTEK network speakers
This integration supports typical surveillance use cases such as alerting intruders, directing crowd flow, and assisting emergency response. VIVOTEK speaks to VORTEX’s intelligence-led approach to proactive deterrence.
Why It Matters
-
Automated Deterrence
Speakers react immediately to VCA events —like intrusion or loitering—without manual intervention. -
Operational Efficiency
Automated messaging cuts reliance on onsite staff and standardizes responses . -
Emergency Management
During crises, such as evacuations or security breaches, speakers can deliver timely instructions—vital for crowd control and safety
Resources & Further Reading
-
Notification: Once the RX9502 is converted to a VORTEX Bridge via firmware update, its original video receiver functionality will be disabled. Please take this into consideration before purchase and deployment.
-
Setup Guide: Refer to the official VORTEX Network Speaker Setup Guide on VORTEX reseller portal for the firmware upgrade SOP and the bridge setup. Or check the set-up document.
-
Feature Insights: See our feature article Top 5 Reasons to Install Network Speakers with VORTEX
-
Real-world case: Smart Surveillance: VORTEX's AI Detection and IP Speaker Deter Suspicious Activity

Tags
Table of Contents